Home > Cybersecurity in Switzerland: Hybrid Clouds, the New Target for Hackers
Cybersecurity in Switzerland is going through a critical period. In 2024, the Federal Office for Cybersecurity (FOCS) recorded around 63,000 cyber incidents, a significant increase compared to the previous year. A cyber incident is now reported every eight and a half minutes. At the same time, Swiss companies are massively adopting hybrid cloud environments for their flexibility and efficiency. However, this digital transformation opens up new vulnerabilities. Cybercriminals are now exploiting the specific weaknesses of these complex architectures. Why this strategic shift by attackers? How can companies protect their infrastructures? This in-depth analysis breaks down the challenges of cloud cybersecurity and offers practical solutions tailored to the Swiss context.

The figures speak for themselves. Switzerland is facing an unprecedented intensification of digital threats affecting all sectors.
In 2024, reports of cyber incidents to the FOCS rose sharply. This increase reveals a worrying trend. Phishing attempts are also exploding, with fraudulent messages now counted in the hundreds of thousands. Businesses are not spared: around 4% of Swiss SMEs have suffered a serious cyberattack over the past three years (State Secretariat for Economic Affairs SECO, 2024), representing approximately 24,000 companies nationwide.
Ransomware attacks remain particularly feared. So-called “CEO fraud” scams are also steadily increasing. These figures demonstrate the growing sophistication of the methods used.
Swiss critical infrastructures are prime targets. The healthcare sector has been hit hard: Rolle hospital saw its IT systems paralyzed in 2023. In industry, several large companies have suffered major attacks involving sensitive data losses. Even telecom giants are not immune to DDoS attacks disrupting their services.
Energy, transport and financial services are also among the most exposed sectors. This diversity of targets shows that no one is safe.
To understand why cybercriminals specifically target hybrid cloud environments, it is first necessary to grasp what they represent and why they appeal to companies.
A hybrid cloud environment combines several components: on-premise servers (private cloud), public cloud services (AWS, Azure, Google Cloud) and sometimes colocation facilities. This architecture offers maximum flexibility. Companies can keep sensitive data in-house while leveraging the power of public cloud for other applications.
In Switzerland, adoption is progressing rapidly. A significant share of Swiss companies already use a hybrid cloud infrastructure or plan to implement one. The federal administration itself is investing heavily through the Swiss Government Cloud project, with a budget of CHF 319.4 million for the period 2025–2032 (Federal Office of Information Technology, 2024).
Unfortunately, the inherent complexity of hybrid cloud creates numerous vulnerabilities. First, the attack surface expands considerably. Each connection between environments represents a potential entry point. Second, management becomes a real challenge. According to recent studies, the vast majority of cloud environments show security gaps caused by configuration errors.
In addition, a significant proportion of Swiss companies lack qualified in-house cloud expertise. Without the right skills, the risk of misconfiguration multiplies. Cybercriminals know this and systematically exploit these weaknesses.

Cybercriminals have adapted their methods to specifically exploit the weaknesses of hybrid cloud architectures. Their techniques are becoming increasingly sophisticated.
Misconfigurations are the main vulnerability. A simple poorly protected test server can become a gateway. A VPN without two-factor authentication, access credentials stolen through phishing… the scenarios are many. Attack campaigns regularly target VPN services in Switzerland, with noticeable increases in intrusion attempts.
Hackers use brute force techniques, multiplying login attempts until they find the right combination. Once inside the network, they can steal confidential data or install malware.
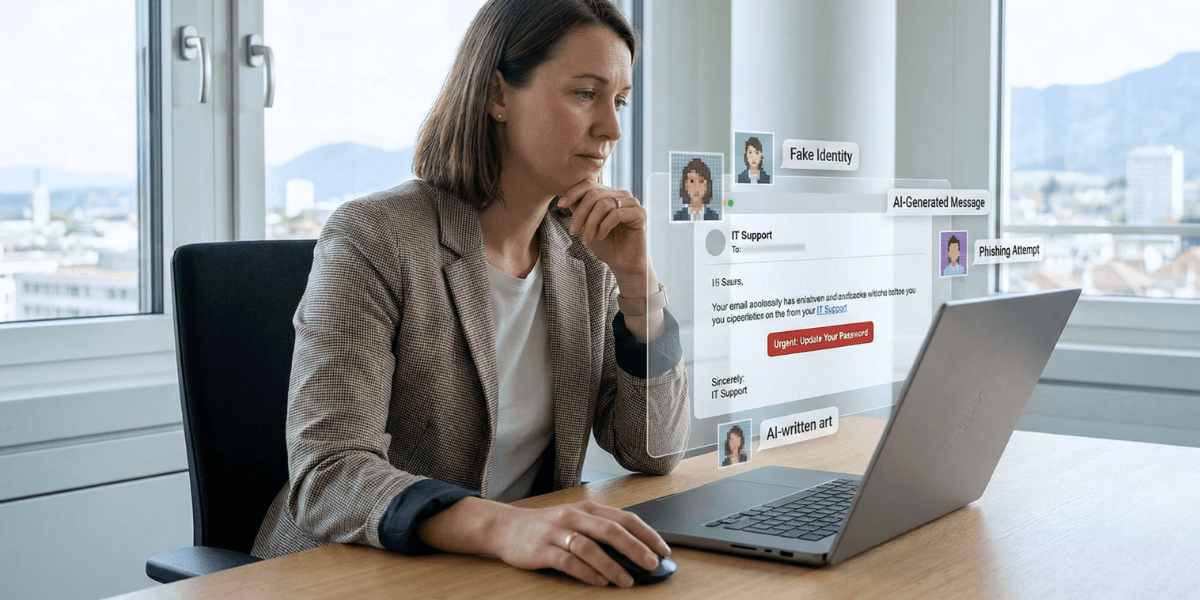
Artificial intelligence is transforming phishing. In 2025, cybercriminals are creating messages that are almost impossible to distinguish from legitimate communications. Phishing cases increase exponentially each year.
Scammers impersonate well-known organizations such as SBB, SwissPass and tax authorities. They also send fake parcel delivery notifications. “Chain phishing” is developing: after compromising an account, criminals send fraudulent messages to all the victim’s contacts.
Ransomware attacks are also evolving. Organized criminal groups first send massive spam, then pose as legitimate support services. Once inside the system, attackers encrypt the data and threaten to publish it if the ransom is not paid. This “double extortion” strategy proves particularly effective.
Cybercriminals specifically target cloud backups. Without an accessible backup copy, companies find themselves with no way out.
Faced with these growing threats, Swiss companies must implement appropriate protection strategies. Several complementary approaches are required.
The Zero Trust principle is based on a simple assumption: never assume trust. Every access must be verified, whether it originates inside or outside the network. This approach requires continuous authentication and the application of the principle of least privilege. In practice, each user receives only the rights necessary for their role, nothing more.
Network micro-segmentation complements this setup. By isolating different parts of the infrastructure, the spread of a potential attack is limited.
A managed Security Operations Center (SOC) provides 24/7 monitoring of the infrastructure. Several specialized Swiss companies offer this type of service. The benefit? Rapid detection of anomalies and immediate incident response. In addition, Swiss companies are increasingly turning to integrated cybersecurity platforms. This consolidation reduces complexity and improves overall visibility.
Automation also plays a crucial role. SIEM tools (Security Information and Event Management) automatically correlate security events from different sources. They detect suspicious patterns that would escape manual analysis.
Regular audits of cloud configurations are essential. Unused ports must be closed systematically and unnecessary services removed. Multi-factor authentication (MFA) should become mandatory for all access. This simple measure blocks the vast majority of intrusion attempts based on stolen credentials.
Encrypting data, both at rest and in transit, adds an extra layer of protection. Even in the event of unauthorized access, the information remains unusable without decryption keys.

Technology alone is not enough. The human factor remains decisive, as a large majority of security incidents involve human error.
Beyond IT specialists, all employees must be trained. Phishing simulations are an excellent educational tool. Several Swiss companies offer dedicated platforms. Employees receive fake fraudulent messages under real conditions. Those who click immediately receive targeted training.
Short and engaging e-learning modules keep attention high. Serious games and cyber challenges make learning more engaging. The goal is to create a true security culture where everyone becomes a strong link in the defense chain.

Switzerland is adapting its legislation to better address cyber threats. Since April 1, 2025, a new obligation has changed the landscape.
Operators of critical infrastructures must now report any cyberattack to the FOCS within 24 hours (Federal Office for Cybersecurity, 2024). This measure applies to the energy, drinking water, transport, healthcare, communications and public safety sectors.
However, exemptions exist. Companies with fewer than 50 employees and turnover below CHF 10 million are exempt. Authorities responsible for communities of fewer than 1,000 people are also excluded.
This obligation has a dual objective: gaining a clearer picture of threats and enabling rapid support for victims. The FOCS can thus coordinate responses and share information on new attack techniques.
Since January 2024, the former National Cybersecurity Centre has become the Federal Office for Cybersecurity, directly attached to the Federal Department of Defence. This change reflects the strategic importance of the issue. The office coordinates the National Cyber Strategy and supports companies in their security efforts.
Given the scale of the threat, budgets are rising sharply. A large majority of Swiss companies have increased their cybersecurity spending in recent years. This trend continues, with further growth expected.
Cloud security is seeing the strongest growth. This investment is not a cost but a necessity. The average damage from a serious cyberattack far exceeds prevention budgets.
Moreover, cyber risks now rank as the top priority for a significant majority of Swiss executives, a figure higher than global and European averages. This awareness is encouraging.
The rise in cyberattacks in Switzerland reveals an unavoidable reality: cybersecurity is no longer an option but a condition for business survival. Hybrid cloud environments, despite their many advantages, create complexity that cybercriminals exploit relentlessly. Configuration errors, lack of visibility, skills shortages: vulnerabilities are numerous.
However, solutions exist. Adopting the Zero Trust model, implementing centralized monitoring, continuously training teams and complying with the new regulatory framework form the pillars of an effective defense. Investment in cloud cybersecurity must be considered strategic, not an expense. The thousands of Swiss SMEs that have suffered serious attacks in recent years prove it: waiting for an incident costs far more than prevention.
Digital transformation offers extraordinary opportunities. But it requires constant vigilance and a methodical approach to security. Swiss companies that integrate this dimension now are building their resilience for the future.
Why are hybrid clouds more vulnerable than traditional infrastructures? Hybrid clouds multiply potential entry points by combining several environments. Management complexity increases the risk of configuration errors, the main cause of vulnerabilities. Overall visibility also becomes more difficult to maintain.
Is my company concerned by the mandatory reporting of cyberattacks? Yes, if you operate in a critical sector (energy, healthcare, transport) and exceed certain thresholds. Companies with fewer than 50 employees and turnover below CHF 10 million are exempt. If in doubt, contact the FOCS.
Which training should IT teams prioritize? The Federal Cyber Security Specialist certificate (51 days, subsidized) for comprehensive training. Microsoft (SC-200), AWS or Azure certifications for targeted skills. Awareness training should involve all employees.
How can you quickly detect an ongoing attack? Watch for these signs: unusual slowdowns, logins from abnormal locations, repeated access attempts, unauthorized changes or sudden traffic spikes. A SIEM or managed SOC automates this detection.

ITTA is the leader in IT training and project management solutions and services in French-speaking Switzerland.
Our latest posts
Subscribe to the newsletter
Consult our confirmed trainings and sessions

Nous utilisons des cookies afin de vous garantir une expérience de navigation fluide, agréable et entièrement sécurisée sur notre site. Ces cookies nous permettent d’analyser et d’améliorer nos services en continu, afin de mieux répondre à vos attentes.
Monday to Friday
8:30 AM to 6:00 PM
Tel. 058 307 73 00
ITTA
Route des jeunes 35
1227 Carouge, Suisse
Monday to Friday, from 8:30 am to 06:00 pm.