Home > What’s Active Directory Actually Used For Today in a Modern Environment?
Active Directory celebrated its 25th anniversary in 2025, yet many consider it outdated technology. With the rise of cloud computing and solutions like Microsoft Entra ID, the question naturally arises: does Active Directory still have a place in our modern infrastructures? The answer might surprise you. Far from being obsolete, AD continues to power nearly 90% of organizations worldwide. From identity management to enhanced security and cloud integration, Active Directory has transformed to meet today’s challenges. Let’s explore why this technology remains essential and how it adapts to today’s hybrid environments.

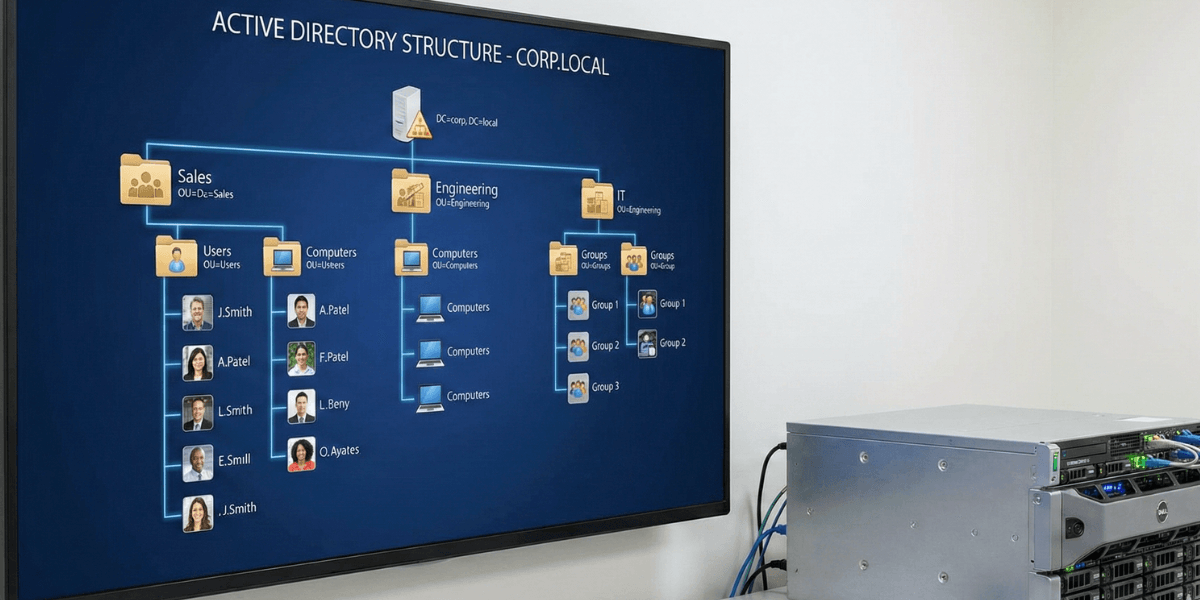
Before exploring its current relevance, let’s recap what Active Directory actually is. It’s a directory service developed by Microsoft for Windows Server systems, allowing organizations to centralize identity and access management.
It functions as an LDAP (Lightweight Directory Access Protocol) directory that stores all information about network resources. Specifically, it catalogs users, computers, groups, printers, and many other objects in a distributed hierarchical database.
This architecture relies on several key components. First, domain controllers (DCs) that host the AD database. Next, the organization into domains, trees, and forests that logically structure the environment. Finally, underlying protocols like Kerberos for authentication, LDAP for queries, and DNS for name resolution.
According to Microsoft’s official documentation, Active Directory provides two fundamental security functions: authentication (verifying identity) and authorization (granting appropriate permissions).
Day-to-day, Active Directory fulfills several essential roles. It enables single sign-on (SSO): users log in once and access all their authorized resources. Group Policy Objects (GPOs) allow centralized deployment of configurations, software, and security settings. For example, a company can enforce password complexity rules or block installation of unauthorized software on all workstations with just a few clicks.
Despite the cloud revolution, Active Directory shows no signs of weakening. Market data is unequivocal. This massive adoption stems from deep integration with the Windows ecosystem, proven maturity and reliability over 25 years, and the human and technical investment already committed by organizations.
The most dependent sectors include finance, healthcare, manufacturing, and public administration. These domains require strict control of identities and access, often with strong regulatory constraints.
The release of Windows Server 2025 provides striking proof of Microsoft’s commitment to Active Directory. This version brings significant improvements: a new functional level, extended NUMA support, database pages increasing from 8K to 32K, and enhanced security. These developments demonstrate that Microsoft considers Active Directory a technology of the future, not a legacy to maintain on life support.

Beyond theory, let’s examine the everyday use cases that justify Active Directory’s presence in contemporary businesses.
Imagine manually managing accounts for 500 employees across multiple sites. Guaranteed nightmare! Active Directory centralizes this management in a single console. Creating an account, modifying permissions, or disabling access upon departure takes just seconds.
This centralization also brings consistency. Password policies, security requirements, and authentication processes remain identical for everyone.
GPOs (Group Policy Objects) represent one of Active Directory’s most powerful features. They allow you to configure thousands of workstations with just a few clicks. Use cases are countless: restricting access to Control Panel, automatic network drive mapping, silent software installation, Windows firewall configuration, desktop customization, and much more.
AD relies on the Kerberos protocol to secure authentication. More robust than the older NTLM, Kerberos uses an encrypted ticket system that limits interception risks. Windows Server 2025 further improves this protocol with new cryptographic features to minimize NTLM usage.
Many enterprise applications rely on Active Directory for authentication. ERPs like SAP, CRMs, document management solutions, or in-house developed business applications integrate naturally with AD via LDAP or Kerberos. This dependency explains why companies can’t simply “flip the switch” on Active Directory.

Confusion often reigns between these two technologies. Yet rather than opposing them, we need to understand their complementarity in modern environments.
Microsoft Entra ID, formerly Azure Active Directory, is the cloud-based identity and access management solution. Unlike on-premises AD, Entra ID is a managed service requiring no physical infrastructure. It uses modern protocols like OAuth 2.0, SAML, and OpenID Connect and integrates seamlessly with Microsoft 365, SaaS applications, and Azure resources.
AD runs on-premises with physical or virtual servers. It uses LDAP and Kerberos for authentication. Microsoft Entra ID lives in Azure cloud and relies on modern web protocols. AD primarily targets traditional Windows applications and local network resources. Entra ID targets cloud applications, SaaS, and mobility scenarios.
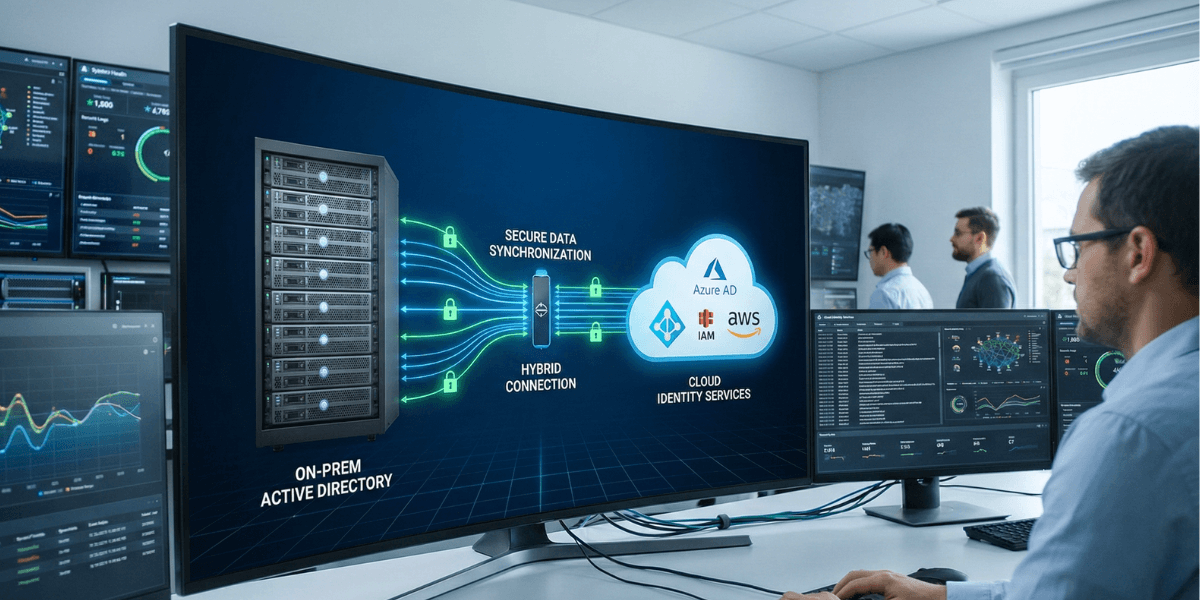
Here’s the truth few dare to say: the majority of organizations need both solutions simultaneously. Employees work with both legacy on-premises applications and cloud tools like Microsoft 365. This hybrid reality has become the de facto standard. Companies synchronize Active Directory with Entra ID using tools like Microsoft Entra Connect.

Hybrid architecture represents today’s dominant model. It combines Active Directory’s robustness with cloud agility, offering flexibility and continuity.
Microsoft Entra Connect serves as the bridge between these two worlds. This tool automatically synchronizes user accounts, groups, and attributes from Active Directory to Entra ID. According to Microsoft Learn, three authentication modes coexist: Password Hash Sync, Pass-through Authentication, and federation via ADFS.
For organizations wanting to migrate to the cloud while maintaining AD compatibility, Azure AD Domain Services offers an interesting alternative. This service provides managed AD features (domain join, GPOs, LDAP, Kerberos) without requiring domain controllers to maintain.
While Active Directory remains so prevalent, it also constitutes a priority target for cyberattackers. Its security therefore represents a major strategic challenge.
The answer comes down to one word: centralization. Active Directory controls access to all company resources. Compromising AD equals obtaining the keys to the kingdom. According to IT Social, nearly 90% of organizations use Active Directory, naturally making it a prime target. Attack techniques have become sophisticated: Pass-the-Hash, Kerberoasting, Golden Ticket, DCSync, etc.
Protecting Active Directory requires a multi-layered approach. Here are the priority measures:
Windows Server 2025 significantly improves default security. LDAP signing becomes required by default, LDAP Channel Binding activates automatically, and reading confidential attributes now requires an encrypted connection.
Among Server 2025’s major innovations, dMSAs (Delegated Managed Service Accounts) deserve particular attention. These accounts protect against Kerberoasting attacks by binding service authentication to a machine’s specific identity.
The release of Windows Server 2025 marks a turning point. For the first time since 2016, Microsoft introduces a new functional level with substantial improvements.
Since Windows 2000, Active Directory used 8K pages for its ESE (Extensible Storage Engine) database. Windows Server 2025 moves to 32K, quadrupling the capacity. Multi-valued attributes can now store up to 3200 values versus 1200 previously. Caution though: activating this optional feature is irreversible.
Until now, Active Directory could only use processors from NUMA group 0, limiting exploitation to 64 cores maximum. Windows Server 2025 lifts this limitation. AD now uses all processors from all NUMA groups. For very large enterprises managing millions of objects, this improvement translates to significant performance gains.
Certain contexts make Active Directory not just relevant, but absolutely necessary.
Swiss hospitals and clinics must meet strict requirements for health data protection. The FADP (Federal Act on Data Protection) imposes sovereignty constraints that complicate exclusive cloud adoption. Additionally, hospital information systems integrate numerous medical devices that communicate via traditional protocols requiring Active Directory.
Factories and industrial facilities use SCADA (Supervisory Control and Data Acquisition) systems that control critical processes. These operational environments (OT) are often isolated from the internet for cybersecurity reasons. Local Active Directory provides authentication without external dependency.
Cantonal and federal administrations in Switzerland manage sensitive and sometimes classified data. Digital sovereignty requires that this information remain under national control. On-premises Active Directory meets these requirements by offering total control over identity infrastructure.

While Active Directory dominates, certain situations justify exploring other options for identity management.
Young cloud-born companies often have no legacy Windows applications. They exclusively use SaaS tools like Google Workspace, Slack, or modern web applications. For them, Microsoft Entra ID alone is entirely sufficient. The absence of Windows Server infrastructure to maintain reduces costs and complexity.
FreeIPA (for Linux) and Samba 4 (AD emulation) offer credible open-source alternatives. These solutions suit organizations with strong Linux skills wanting to avoid Microsoft dependency. However, compatibility isn’t always perfect with all Windows applications.
The investments in Windows Server 2025 prove that Microsoft doesn’t consider Active Directory dying technology. On the contrary, the publisher is adapting AD to the realities of modern hybrid environments.
Coexistence between Active Directory and Microsoft Entra ID will become the standard for at least the next decade. Organizations will gradually migrate certain workloads to the cloud while maintaining AD for critical on-premises needs. This progressive evolution allows infrastructure modernization without major disruption.

So what is Active Directory really used for today? The answer is clear: far more than we might imagine. Far from being a relic of the past, AD remains the foundation of identity infrastructure for millions of businesses worldwide, including in Switzerland.
The innovations brought by Windows Server 2025 demonstrate Microsoft’s commitment to this technology. Rather than disappearing, Active Directory is evolving to integrate harmoniously into modern hybrid environments. It coexists with Microsoft Entra ID, each meeting specific needs: AD for local control and legacy applications, Entra ID for cloud and mobility.
The real question therefore isn’t “should we keep Active Directory?” but “how do we intelligently integrate it into a modern identity strategy?” For the majority of organizations, the answer lies in a well-designed hybrid architecture that’s secure and scalable. Active Directory certainly hasn’t had its last word.
Will Active Directory disappear in the coming years?
No, Microsoft continues to invest heavily in Active Directory as proven by Windows Server 2025 with its new functional level. Legacy Windows infrastructures depend too heavily on AD to envision disappearance in the short or medium term. The horizon is measured in decades rather than years.
Can you really replace Active Directory with Microsoft Entra ID alone?
It depends entirely on context. 100% cloud companies with modern SaaS applications can operate solely with Entra ID. However, organizations with legacy Windows applications, regulatory constraints, or industrial systems will need on-premises Active Directory for a long time.
What’s the main difference between a domain controller and Microsoft Entra ID?
An Active Directory domain controller is a physical or virtual server that the organization installs and maintains itself. Microsoft Entra ID is a cloud service fully managed by Microsoft, with no infrastructure to manage. One offers total control and local latency, the other simplicity and cloud scalability.
Do GPOs work with Microsoft Entra ID?
Traditional GPOs are specific to on-premises Active Directory. Microsoft Entra ID uses a different system: compliance policies and conditional access via Microsoft Intune to manage devices. In a hybrid environment, both systems coexist with complementary roles.

ITTA is the leader in IT training and project management solutions and services in French-speaking Switzerland.
Our latest posts
Subscribe to the newsletter
Consult our confirmed trainings and sessions

Nous utilisons des cookies afin de vous garantir une expérience de navigation fluide, agréable et entièrement sécurisée sur notre site. Ces cookies nous permettent d’analyser et d’améliorer nos services en continu, afin de mieux répondre à vos attentes.
Monday to Friday
8:30 AM to 6:00 PM
Tel. 058 307 73 00
ITTA
Route des jeunes 35
1227 Carouge, Suisse
Monday to Friday, from 8:30 am to 06:00 pm.